Cyber threats are constantly growing, with the most dynamically developing criminal use of AI, the “ransomware service” package, and data theft using malware. The CSIRT KNF team has just presented a report summarizing the trends observed in 2025.

“The Financial Sector Threat Landscape” is the title of a report published in late April by the cybersecurity team at the Polish Financial Supervision Authority. The document summarizes the most important problems that financial institutions face in the digital world. Only a few of them are directly related to clients.
5 Groups of Threats – from APT to Employee
Banks, insurers, and brokerage firms are threatened by the actions of several groups of “stakeholders.” The first are state-sponsored groups (APTs) , teams that, at the request of their principals, seek to disrupt the operation of strategic sectors of the economy and obtain politically valuable information. APTs use cybersabotage, spear phishing, undocumented software vulnerabilities, and supply chain attacks as entry points into key systems.
The second type of threat is organized crime groups . Here, the goal of the activity is mainly financial, and the criminals operate almost like corporations. They create packages of “services” sold to anyone willing (e.g. ransomware as a service), banking Trojans, operate platforms for trading payment card data, and install software for mining cryptocurrencies (cryptojacking) on victims.
In addition to criminal “businesses”, there is no shortage of individual cybercriminals on the market. Those who operate independently are primarily driven by the desire for profit. Sometimes the motives are personal (revenge, seeking recognition in the community) or ideological. Their arsenal includes phishing, malware, ransomware, and social engineering tricks for identity theft.
Hacktivists attack financial institutions for completely different reasons – ideological or political. “Pro-Russian groups constitute a significant segment of this environment, often operating as part of unofficial support for Russian interests,” the report notes. Hacktivists use DDoS attacks that block websites and network services, replace the content of services (defacement), reveal sensitive data of their victims (doxing), and spread disinformation.
The report also points to a non-obvious type of actor threatening the cybersecurity of financial institutions – internal users, employees, co-workers . Sometimes they act with premeditation, and sometimes through negligence they endanger the resources of their employers.
Hits of 2025 – where evolution is the fastest
CSIRT KNF specialists draw attention to several particularly rapidly developing types of attacks. The use of tools based on artificial intelligence is becoming increasingly common, especially deepfake technology. It is used for more advanced phishing (e.g. a bank employee is called by a “director”), impersonating a bank, but also reputational attacks (false materials slandering representatives of the institution). “AI attacks, including deepfakes, are still relatively new, but their frequency is growing with the development of technology” – it is indicated in the document.
Ransomware as a service is, in turn, a form of “industrialization” of one of the forms of cybercrime. Ransomware is malicious software that, for example, encrypts user data and then demands a ransom for a key that allows the recovery of files. Criminals do not have to prepare such campaigns themselves today, they can use ready-made solutions, where for an appropriate fee you receive all the tools, as well as, for example, access to online “technical support.”
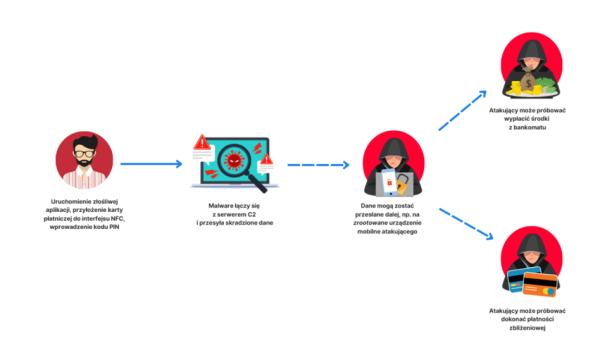
NFC Relay attack scheme (CSIRT KNF)
The report also describes a relatively new type of threat, previously known only from theoretical considerations. NFC Relay malware relies on persuading the victim to read the contactless card via the NFC module in the phone, and then redirecting this data to attempt to make a payment or withdraw from an ATM. The pretext could be, for example, “customer verification” in a fake mobile application.
On the Polish market, only one case of this scheme being used has been recorded so far, and the campaign was aimed at PKO BP clients. “A similar attack model, expanded with a social engineering thread and the use of PWA technology in the first phase of the campaign, was observed in Q3 2024 in the Czech Republic,” the report indicates, referring to a broader description of the method. The scheme has significant limitations, but “over time, we can expect the above technique to become more widespread among attackers targeting the Polish market,” experts emphasize.